Passwords, Security and the Future of Authentication [#Infographic]
Are passwords dead?
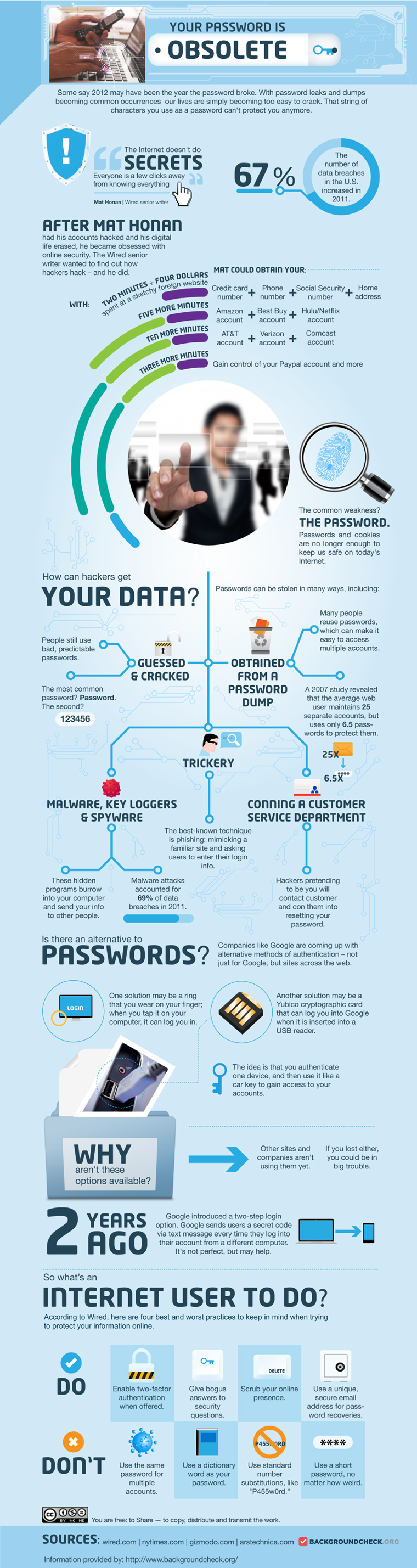
According to Wired's Mat Honan, they ought to be. Honan is the technology journalist who was hacked last year. In just a few minutes, his entire digital life, including photos of his young daughter, disappeared. If it can happen to a tech-savvy writer like Honan, it can happen to anyone.
When it comes to authentication, most IT departments and end users trade security for convenience. Trying to remember long, complex passwords and using multifactor authentication is a pain and makes accessing data, e-mail and applications difficult. As the web has evolved, users tend to have user names and passwords for dozens, maybe even hundreds, of websites and applications. The cloud, while solving many problems, creates a new one: Our data is protected by only a password, with multiple points of failure. This, Honan says, is a huge part of the authentication problem:
During the formative years of the web, as we all went online, passwords worked pretty well. This was due largely to how little data they actually needed to protect. Our passwords were limited to a handful of applications: an ISP for email and maybe an ecommerce site or two. Because almost no personal information was in the cloud—the cloud was barely a wisp at that point—there was little payoff for breaking into an individual’s accounts; the serious hackers were still going after big corporate systems.
So we were lulled into complacency. Email addresses morphed into a sort of universal login, serving as our username just about everywhere. This practice persisted even as the number of accounts—the number of failure points—grew exponentially. Web-based email was the gateway to a new slate of cloud apps. We began banking in the cloud, tracking our finances in the cloud, and doing our taxes in the cloud. We stashed our photos, our documents, our data in the cloud.
Read Kill the Password: Why a String of Characters Can’t Protect Us Anymore on Wired.
IT departments have to take all of the potential failure points into consideration when measuring security. Bring-your-own-device (BYOD) programs have complicated mobile security, because users take on more of the responsibility. One of the riskiest points of failure is the user — not the technology. The infographic below outlines how hackers access data and how to stay safe online.
This infographic originally appeared on BackgroundCheck.org.








